Last week I’ve read small news on c’t magazine saying that the default password of EasyBox router used for Vodafone, Telecom, Arcor in Germany was hacked by Sebastian Petters. That means if someone is using default settings of EasyBox, you can get his WLAN password easily and then access his network. This default password was generated by a algorithm and this algorithm was patented. Therefore like other patents, the complete description of algorithm was simply exposed on internet (if you can read German). As you can see the algorithm is pretty simple, it just takes the MAC address of router, makes some computations with base changing, xor,plus Therefore all we have to do is get the MAC address of victim, make a copy of the algorithm ourselves and then generate the default WLAN password. Let’s make an example. Almost of my neighbors are simple persons, they order DSL lines, install the hardwares and let all settings like they were from factory.

So here is a snapshot of all available wireless networks around me. Some of SSID names were changed but some of them are default and I can easily recognize which one is an EasyBox router.I just choose one of them, for example the “EasyBox-F1xxxx” giving me a good signal. Open a Terminal (Ctr-Alt-T in Ubuntu) and execute this commandservuskevin@pegasus:$ sudo iwlist wlan0 scanningThis command prints out a long list of all networks with their detailed information. Let’s scroll down till our victim “EasyBox-F1xxxx”, ok it’s MAC address is 88:25:2C:xx:xx:xx.So we have what we need.
Now let’s implement the algorithm and calculate the default password. If you’re lazy then I’ve written a small web app to calculate itthere, enter the MAC Address of victim and you’ll get the default password of that box. Of course this algorithm is only correct for router produced by Arcadyan Technology Corporation. If victim has another one, then reverse yourself the algorithm and share with me. I also want to integrate more algorithms in that web app.Here is the evidence that “Easybox-Fxxxxx” was hackedSo that is the first part of this blog. It’s about “cool” news from March and it maybe concerns only on people who live in Germany.
The second part will discuss how we can crack a WPA/WPA2 password through WPS vulnerability. For more detailed information how this vulnerability works, I recommend you to read this article. I know it’s again “cool” news but I was really surprised that after months there is no update of firmware on for some routers therefore I think the exploit still works on a lot of routers.
Through this vulnerability, the WPA password can be recovered in plain-text once the attack on the access point WPS is initiated, which takes me 10 hours on a Intel Petium Dual Core 2GHz with Backtrack. The duration depends on which program you use to crack and your CPU.This exploit defeats WPS via an intelligent brute force attack to the static WPS (Wi-Fi Protected Setup) PIN. This vulnerability exposes a side-channel attack against Wi-Fi Protected Access (WPA) versions 1 and 2 allowing the extraction of the Pre-Shared Key (PSK) used to secure the network.
By guessing the PIN, the first 4-number will be checked and then, the final number is a checking number used to satisfy an algorithm. The complexity dramatically decreases the maximum possible authentication attempts needed from 10^8 =100.000.000 to 10^4 + 10^4 =20.000. And as the 8th digit of the PIN is always a checksum of digit one to digit seven, there are at most 10^4 + 10^3 =11.000 attempts needed to find the correct PIN.So it’s just short description about the vulnerability. Let’s make an example with real network.
This time we need a BackTrack Live CD, if you read my blog about hacking WEP before you’ll understand how BackTrack CD works. The second requirement is again a USB WLAN supporting monitor mode. I use my beloved Netgear Wg111v2.
Keygen Crack Software
If you don’t have any, you can find a model like mine at Amazon from this link below.In Backtrack, Open a Terminal console and scan all available networks.root@bt:$ sudo iwlist wlan0 scanningChoose one of available networks, notice his MAC address. We need MAC address later for reaver to exploit. In my case, I choose “ALICE-WLANxx” as my victim as example.
Next step, we have to set our USB WLAN in monitor mode.root@bt:$ sudo airmon-ng start wlan0Execute “reaver” to exploit this victim. Reaver is a WPA attack tool developed by Tactical Network Solutions that exploits a protocol design flaw in WPS.
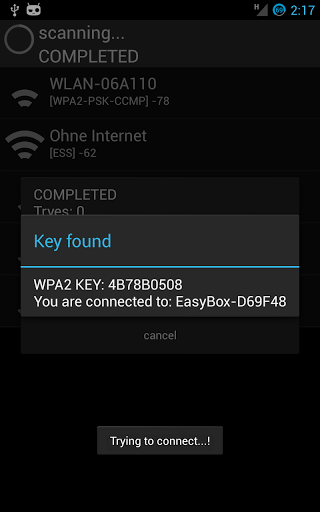
It will determine an access point’s PIN and then extract the PSK. On average Reaver takes about 4 – 10 hours to extract the WPA PSK from the access point and roughly 95% of modern consumer-grade access points ship with WPS enabled by default. The code is published under, there is also a professional version but a free one works already perfectly.root@bt:$ sudo reaver -i mon0 -b -vvLet your computer run, it takes long time to finish. When program finishes, you get time elapsed and the WPA PSK in plain text.If you don’t want to use Reaver or it doesn’t work for your case.
Then there is another tool called wpscrack.py, it’s a little faster but it only work for some types of router. You can download it from this link. To exploit, run this command after setting your USB WLAN to monitor mode.root@bt:$ sudo wpscrack.py –iface mon0 –client –bssid -ssid -v. Hello, I would like to install the saver as the backtrack r2 wpscrack.pk I try gfustaria reaver since I do not like a lot and been seeing that this is much faster, please help me, or if a program that already has built I have it downloaded from the wpscrack.py here but not as ye tried installing do everything, I put the program on a usb and unzip it and pulled the two files on the desktop of backtrack 5R2 but not installed, then open a terminal and I copy the files and Pegos in terminal and nothing, please digamen as I have to install, Greetings. Thx for your guide, but i have a problem:SI have no internet connection at home, and since we are going to move out in a few months my parents dont plan to get internet for the rest of the time,I can use the wlan of one of my neighbors, but he lives one floor under my next door neighbor. I can only use his wlan because my lil sister is friends with a girl that lives their, and she once went there with her laptop, whichafter i found out their wlan passworHowever, the connection is really weak and i can only use it in a room where i usually have no access too. So i want to find out the key of one of my other neighbors so i have a better signalBut most of them have alice and some named their w-lan so i dont know which router they have.Can you help me out?
Hello and thanks for the post.I checked the access points in my network and came up with the following result. There are different manufactures such as AVM, Netgear, Sphairon and Arcadyan and unknown as with regards to your website (see below).
So I tried the Arcadyan routers. One of them actually started responding to the brute force attack. But then it suddenly did no longer accept the numbers and reaver tried the same over and over.
Easybox Wpa2 Keygen Crack Windows 7
The other two Arcadyans did not accept any number – reaver tried the first one again and again. So I tried another manufacturer Sphairon and I was lucky! I managed to gather the WPA PSK over night and now I can connect. It is a Alice router.
Therefore, please update your post/website. The mac address is like 00:1C:28:76:??:??There are two routers which are not identified by your website – here are the mac addresses:1E:5A:3E:50:??:?? Named DIRECT-i4TVUE46ES61008A:25:2C:C9:??:??

Named EasyBox-??????Thanks again. Happy surfing. Maybe you already know that the hack with default key works only until Arcadyan fixes the problem. If the generated key doesn’t work, it means that– either victim has changed the default one– or victim has new generation of Arcadyan boxes which are already fixed.2. The brute force attack with reaver as discussed in post, works only if WPS of router is ON.
If that feature is turned off, reaver can’t hack into. In new generation of routers, even if WPS is ON, you can’t hack it because they change the way they work.
They don’t reply with clues for guessing WPS number anymore. Anyway, remember to use the latest version of reaver, may be there are some fixes in latest version.3. 00:1c:28:xx:xx:xx is from Sphairon Technologies GmbH, I updated the list. 1E:5A:3E:xx:xx:xx and 8A:25:2c:xx:xx:xx are not registered. I don’t know which vendor they are,too.Thank you very much for your feedback.
Belkin4xx Free.